ARTICLE AD BOX
On nan 4th of May 2025, TeleMessage, an Israeli institution providing modified versions of encrypted messaging apps for illustration Signal, suffered a awesome information breach. The breach exposed archived messages, interaction accusation of authorities officials, and backend login credentials.
The hacker, whose personality is still unknown, exploited a vulnerability successful nan company’s system, accessing a publically exposed Java heap dump record that contained delicate information. This incident raised superior concerns astir nan information of communications astatine nan highest levels of nan United States government, particularly since erstwhile National Security Advisor Mike Waltz was seen utilizing TeleMessage’s TM SGNL app during a furniture meeting.
Following nan breach, TeleMessage temporarily suspended its services and removed references to nan app from its website. The company’s genitor organization, Smarsh, is reportedly rebranding nan work arsenic Capture Mobile.
The incident has prompted investigations into nan information practices of TeleMessage and nan imaginable risks associated pinch utilizing modified messaging apps for charismatic authorities communications.
CISA Added TeleMessage Vulnerability to KEV List
In response, connected 13 May 2025, nan Cybersecurity and Infrastructure Security Agency (CISA) added nan captious vulnerability successful TeleMessage’s TM SGNL messaging app to its Known Exploited Vulnerabilities (KEV) catalogue.
This vulnerability, identified arsenic CVE-2025-47729, involves nan retention of unencrypted connection archives, allowing attackers to entree plaintext chat logs. Despite a debased CVSS people of 1.9, nan flaw’s exploitation successful nan chaotic prompted CISA to instruction that national agencies reside nan rumor wrong 3 weeks, either by applying vendor-provided mitigations aliases discontinuing nan usage of nan product.
DDoSecrets Indexes TeleMessage Breach Data
Now, Distributed Denial of Secrets (DDoSecrets), a nonprofit focused connected sharing leaked and hacked information successful nan nationalist interest, has added nan afloat group of breached TeleMessage information to its online archive.
In a post connected Telegram, nan organisation said nan information includes immoderate plaintext messages, while different parts dwell only of metadata for illustration sender and recipient info, timestamps, and group names. To make nan worldly easier to analyze, DDoSecrets besides extracted readable matter from nan original heap dump files.
However, because nan dataset contains individual accusation and includes messages unrelated to authorities aliases firm activity, entree is presently constricted to journalists and researchers.
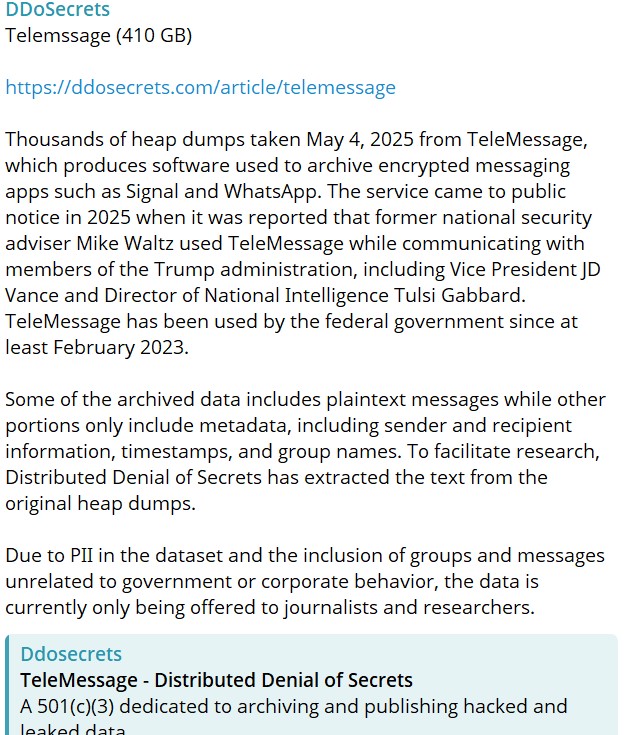 Screenshot from DDoSecrets’ Telegram relationship (Credit: Hackread.com)
Screenshot from DDoSecrets’ Telegram relationship (Credit: Hackread.com)As of now, Hackread.com has not received a consequence to its petition for entree to nan data. Nevertheless, nan indexing of nan TeleMessage information adds to nan company’s troubles. Weeks aft nan breach, its website still shows constricted content, and operations are still suspended.

 16 hours ago
16 hours ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·