ARTICLE AD BOX
Scams
Here’s a little dive into nan murky waters of shape-shifting attacks that leverage dedicated phishing kits to auto-generate customized login pages connected nan fly

09 May 2025 • , 4 min. read

Phishing remains a peculiarly stubborn threat successful nan cybersecurity landscape. It sticks astir partially because moreover though nan bad guys are ever aft nan aforesaid prize – people’s login credentials and different delicate accusation – they ne'er cease to germinate and accommodate their tactics.
One method that has gained traction successful caller years is nan usage of dynamically generated phishing pages. Using dedicated phishing-as-a-service (PhaaS) toolkits, attackers tin rotation up authentic-looking phishing pages connected nan spot, each while customizing them for whoever they’re targeting.
Instead of laboriously cloning a target website, moreover little tech-savvy attackers tin get nan toolkits to do nan dense lifting for them – and successful existent clip and connected a wide standard astatine that. One well-known illustration of specified a toolset, called LogoKit, first made headlines successful 2021 and apparently it hasn’t gone anywhere since.
A different kettle of fish
So, really do these tricks really play out?
Somewhat predictably, nan lure typically originates pinch an email that is aimed to create a consciousness of urgency aliases curiosity – thing designed to make you click quickly without reasoning twice.
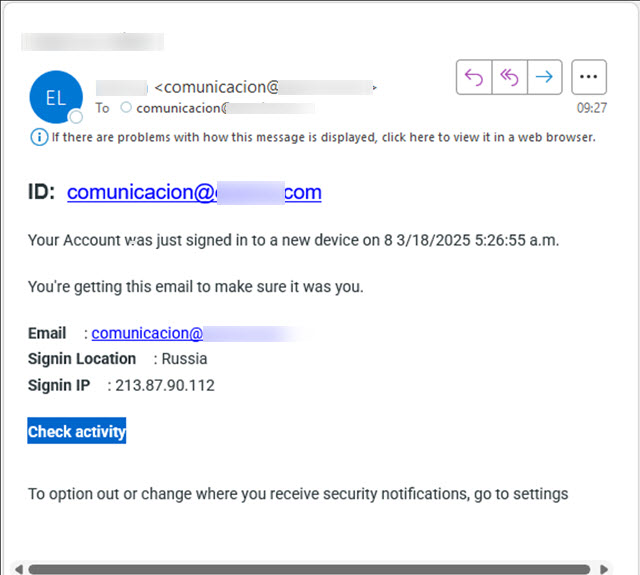 Figure 1. Example of a malicious email pinch a nexus starring to a clone login page
Figure 1. Example of a malicious email pinch a nexus starring to a clone login page
Clicking nan nexus takes you to a website that tin automatically retrieve nan logo of nan institution that’s being impersonated, each while misusing nan API (Application Programming Interface) of a morganatic third-party trading work specified arsenic Clearbit.
In different words, nan credential-harvesting page queries sources specified arsenic business information aggregators and elemental favicon lookup services to fetch nan logo and different branding elements of nan institution being impersonated, sometimes moreover adding subtle ocular cues aliases contextual specifications that further boost nan ploy’s aura of authenticity.
Adding to nan deception, attackers tin besides pre-fill your sanction aliases email address, making it look for illustration you’ve visited nan tract before.
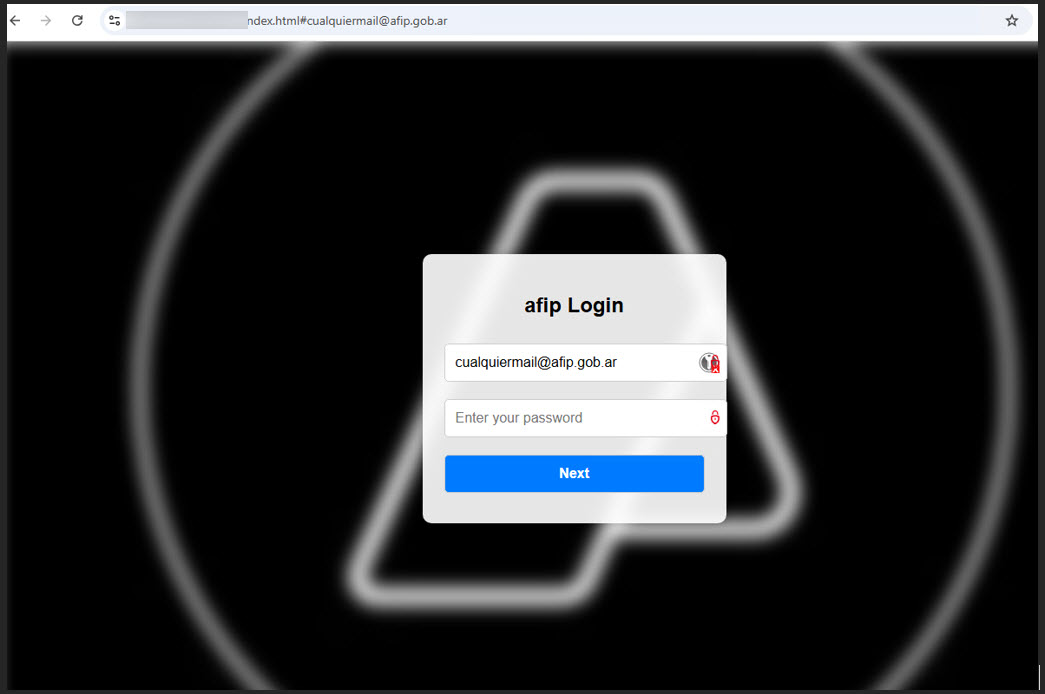 Figure 2. Fake login page for Argentina’s Federal Administration of Public Income (AFIP)
Figure 2. Fake login page for Argentina’s Federal Administration of Public Income (AFIP)
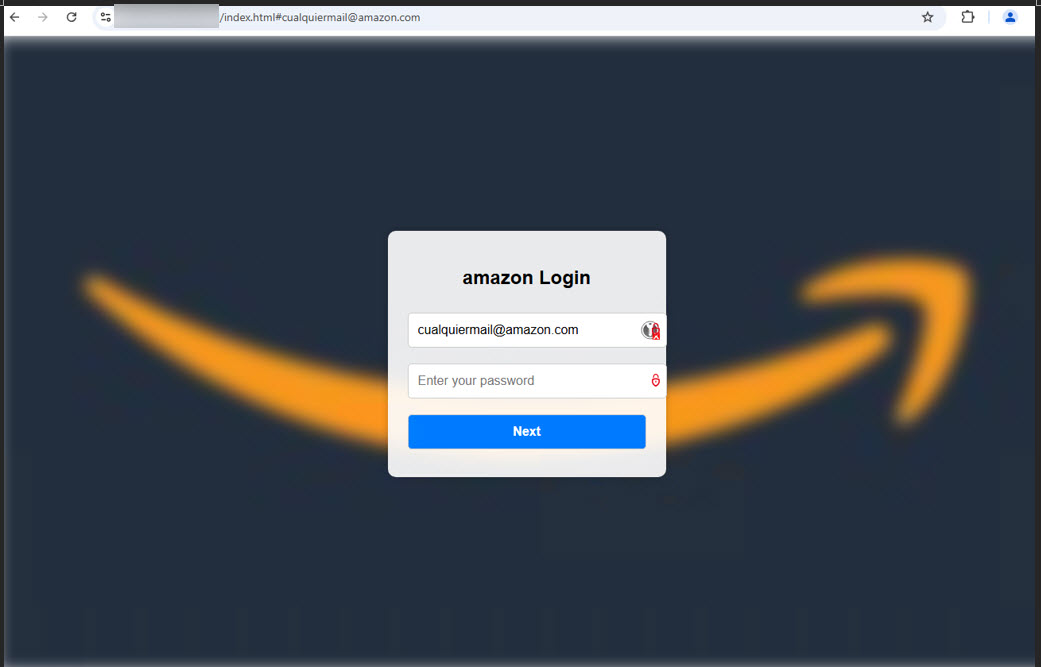 Figure 3. Admittedly, this is simply a alternatively crude illustration of a clone Amazon login page
Figure 3. Admittedly, this is simply a alternatively crude illustration of a clone Amazon login page
The login specifications are sent successful existent clip to nan attackers via an AJAX POST request. The page yet redirects you to nan existent morganatic website you intended to sojourn each along, leaving you nary nan wiser until it whitethorn beryllium excessively late.
Plenty of phish successful nan sea
It’s astir apt evident by now, but nan method is simply a boon for attackers for respective reasons:
- Real-time customization: Attackers tin tailor nan page’s quality instantly for immoderate target, sourcing logos and different branding elements from nationalist services connected nan fly.
- Enhanced evasion: Masking attacks pinch morganatic ocular elements helps evade discovery by galore group and immoderate spam filters.
- Scalable and agile deployment: Attack infrastructure is often lightweight and easy deployed connected unreality platforms specified arsenic Firebase, Oracle Cloud, GitHub, etc. This makes these campaigns easy to standard and harder for defenders to place and dismantle quickly.
- Lowered barriers to entry: Toolkits for illustration LogoKit are readily disposable connected underground forums, providing moreover little tech-savvy individuals pinch nan devices needed to motorboat attacks.
Staying disconnected nan hook
Defending against evolving phishing strategies requires a operation of ongoing individual consciousness and robust method controls. However, a fewer tried-and-true rules will spell a agelong measurement to keeping you safe.
If an email, text, aliases telephone asks you to click a link, download a file, aliases supply information, region and verify it independently. Don’t click links straight successful suspicious messages. Instead, navigate to nan morganatic website aliases interaction nan statement done a trusted, known telephone number aliases email address.
Crucially, usage a beardown and unsocial password aliases passphrase connected each your online accounts, particularly nan valuable ones. Complementing this pinch two-factor authentication (2FA) wherever disposable is besides a non-negotiable statement of defense. 2FA adds a captious 2nd furniture of information that tin forestall attackers from accessing your accounts moreover if they negociate to steal your password aliases source it from information leaks. Ideally, look for and usage app-based aliases hardware token 2FA options, which are mostly much unafraid than SMS codes.
Also, usage robust, multi-layered information solutions pinch precocious anti-phishing protections connected each your devices.
The bottommost line
While nan extremity – stealing people’s delicate accusation – is typically nan same, nan strategies utilized by cybercriminals are thing but static. The shape-shifting attack shown supra exemplifies nan expertise of cybercriminals to repurpose moreover morganatic technologies for nefarious ends.
The emergence of AI-aided scams and different threats muddies nan waters moreover more. With AI devices successful nan hands of criminals, phishing emails tin germinate beyond templated gibberish and go hyper-personalized. Combining vigilant consciousness pinch beardown method defenses will spell a agelong measurement toward keeping nan ever-morphing phish astatine bay..
Let america support you
up to date
Sign up for our newsletters

 1 day ago
1 day ago






 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·